A good deal of web3 security rests on blockchains’ special ability to make commitments and to be resilient to human intervention. But the related feature of finality – where transactions are generally irreversible – makes these software-controlled networks a tempting target for attackers. Indeed, as blockchains – the distributed computer networks that are the foundation of web3 – and their accompanying technologies and applications accrue value, they become increasingly coveted targets for attackers.
Despite web3’s differences from earlier iterations of the internet, we’ve observed commonalities with previous software security trends. In many cases, the biggest problems remain the same as ever. By studying these areas, defenders – whether builders, security teams, or everyday crypto users – can better guard themselves, their projects, and their wallets against would-be thieves. Below we present some common themes and projections based on our experience.
- Following the money
- Attackers generally aim to maximize return on investment. They can expend more time and effort attacking protocols with more “total value locked,” or TVL, because the potential rewards are greater.
- The most well-resourced hacker groups target high value systems more often. Novel exploits, the most valuable kind, are more frequently aimed at these prized targets too.
- Low cost attacks – like phishing – will never go away, and we expect them to become more common for the foreseeable future.
- Patching the holes
- As developers learn from tried-and-true attacks, they may improve the state of web3 software to the point where it becomes “secure by default.” Often, this involves tightening up application programming interfaces, or APIs, to make it harder for people to mistakenly introduce vulnerabilities.
- While security is always a work in progress – and to be sure, nothing is ever hack-proof – defenders and developers can raise the cost of attacks by eliminating much of the low hanging fruit for attackers.
- As security practices improve and tooling matures, the success of the following attacks may drop substantially: governance attacks, price oracle manipulation, and re-entrancy bugs. (More on these below.)
- Platforms that are not able to ensure “perfect” security will have to use exploit mitigation efforts to lower the possibility of losses. This may deter attackers by reducing the “benefit,” or upside, part of their cost-benefit analysis.
- Categorizing attacks
- Attacks on different systems can be classified based on their shared characteristics. Defining traits include how sophisticated an attack is to pull off, to what extent the attacks can be automated, and what prevention measures can be put in place to defend against them.
Below is a non-exhaustive list of attack types we’ve seen in the largest hacks over the past year. We’ve also included our observations on today’s threat landscape and where we expect web3 security to go in the future.
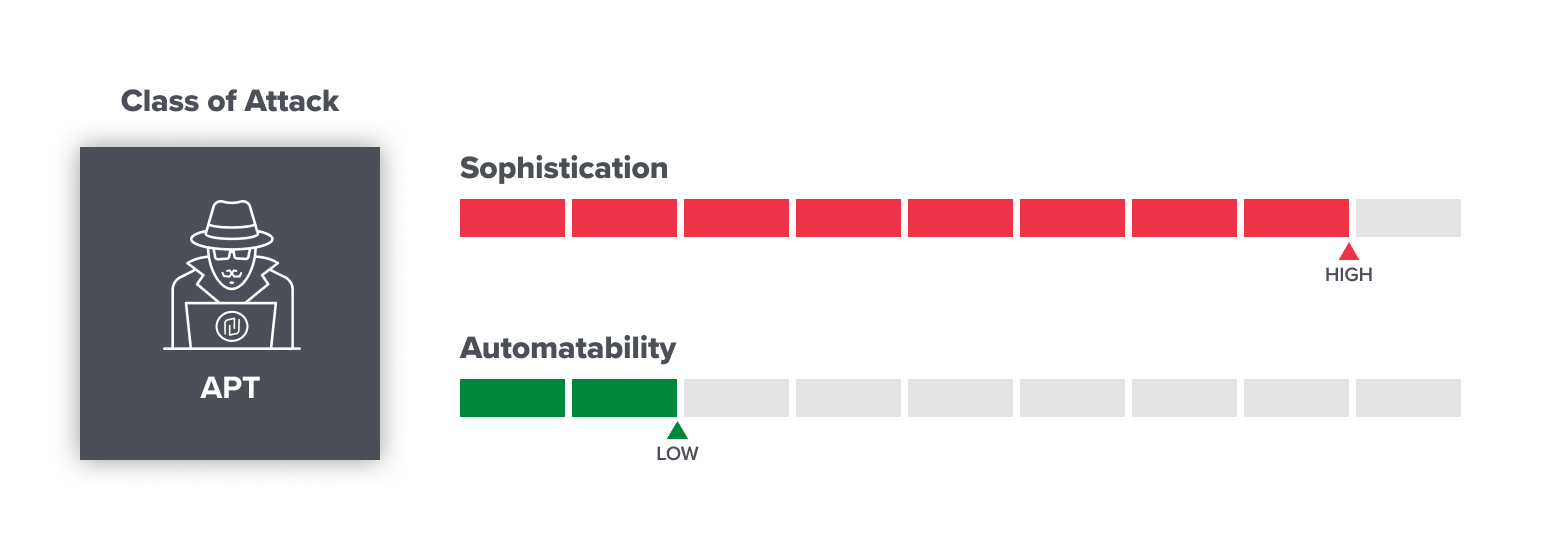
APT operations: the top predators
Expert adversaries, often called Advanced Persistent Threats (APTs), are the boogeymen of security. Their motivations and capabilities vary widely, but they tend to be well-heeled and, as the moniker suggests, persistent; unfortunately, it’s likely they will always be around. Different APTs run many different types of operations, but these threat actors tend to be the likeliest to attack the network layer of companies directly to accomplish their goals.
We know some advanced groups are actively targeting web3 projects, and we suspect there are others who have yet to be identified. The people behind the most concerning APTs tend to live in places without extradition treaties with the U.S. and EU, making it harder for them to be prosecuted for their activities. One of the most well-known APTs is Lazarus, a North Korean group which the FBI recently attributed as having conducted the largest crypto hack to date.
- Examples:
- Ronin validator hack
- Profile
- Who: Nation states, well-funded criminal organizations, and other advanced organized groups. Examples include Ronin hackers (Lazarus, widely linked to North Korea).
- Sophistication: High (only available to highly resourced groups, usually in countries that won’t prosecute).
- Automatability: Low (still mostly manual efforts with some custom tooling)
- Expectations for the future: APTs will remain active as long as they can monetize their activities or achieve various political ends.
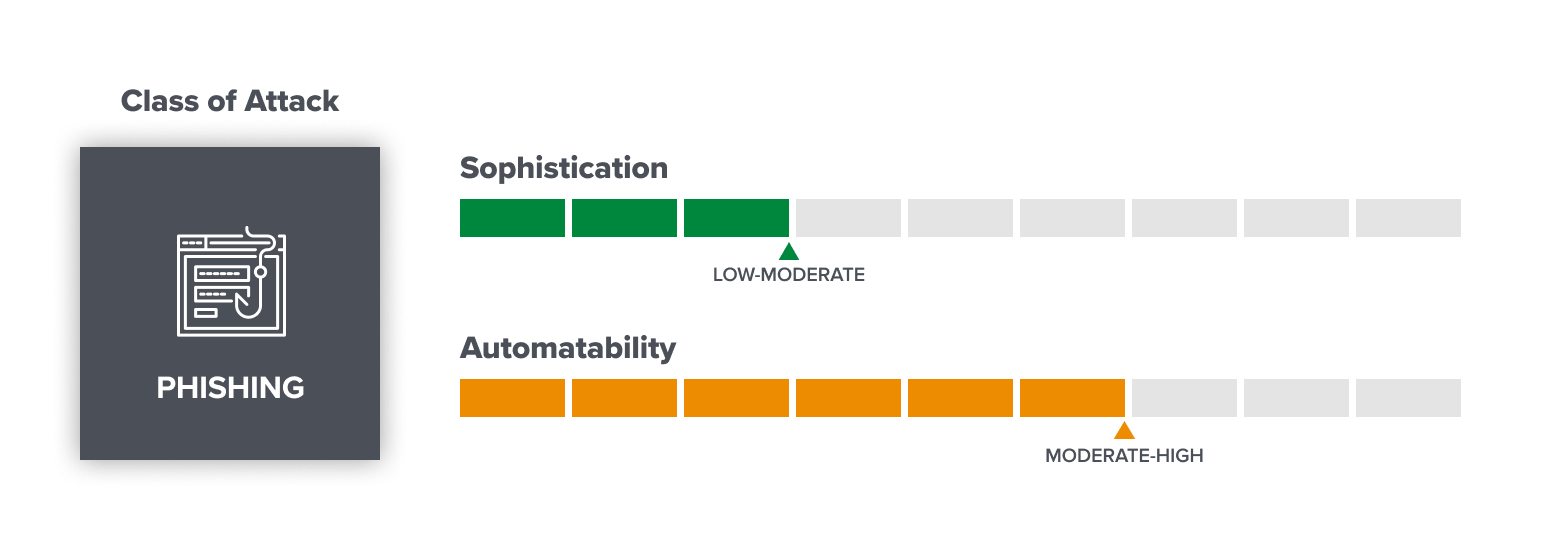
User-targeted phishing: the social engineers
Phishing is a well-known, ubiquitous issue. Phishers try to ensnare their prey by sending baited messages through a variety of channels, including instant messenger, email, Twitter, Telegram, Discord, and hacked websites. If you browse your spam mailbox you’ll probably see hundreds of attempts to trick you into divulging information, like passwords, or to steal your money.
Now that web3 lets people directly trade assets, such as tokens or NFTs, with almost instant finality, phishing campaigns are targeting its users. These attacks are the easiest way for people with little knowledge or technical expertise to make money stealing crypto. Even so, they remain a valuable method for organized groups to go after high-value targets, or for advanced groups to wage broad-based, wallet-draining attacks through, for example, website takeovers.
- Examples
- Profile
- Who: Anyone ranging from script kiddies to organized groups.
- Sophistication: Low-Moderate (attacks can be low quality “spray-and-pray” or hyper-targeted depending on the effort put in by attackers).
- Automatability: Moderate-High (most of the work can be automated).
- Expectations for the future: Phishing is cheap and phishers tend to adapt to – and route around – the latest defenses, so we expect incidences of these attacks to rise. User defenses can be improved through increased education and awareness, better filtering, improved warning banners, and stronger wallet controls.
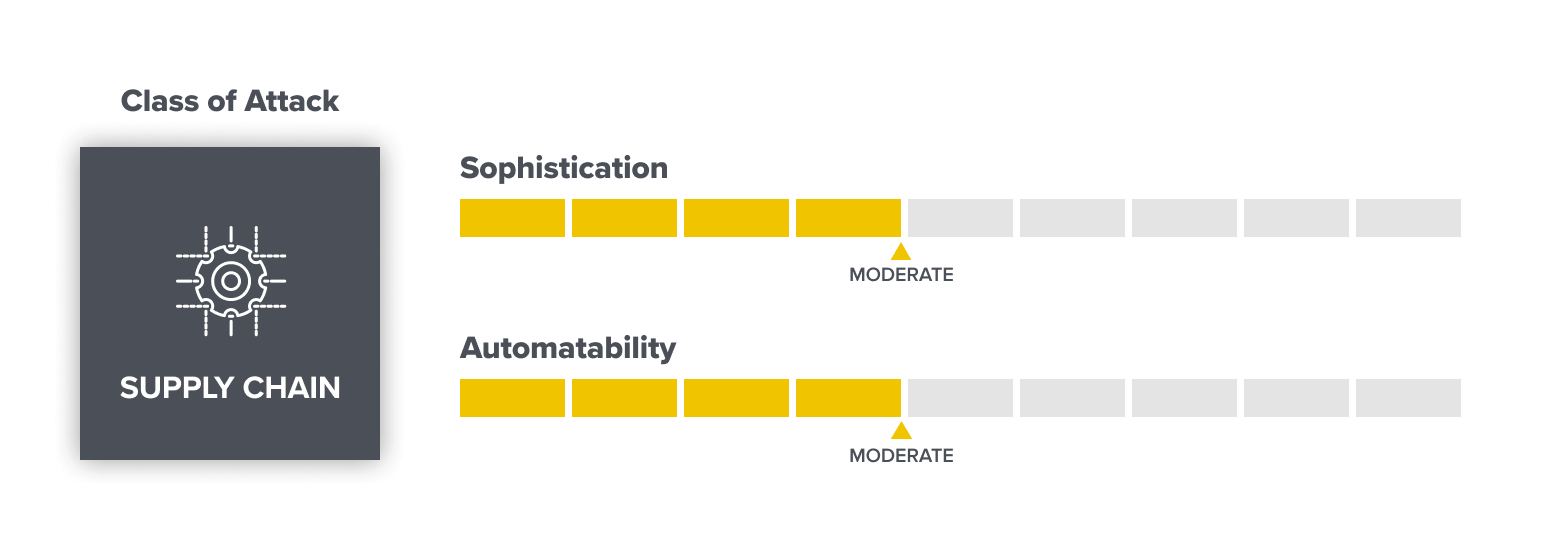
Supply chain vulnerabilities: the weakest links
When car manufacturers discover defective parts in vehicles, they issue safety recalls; it’s no different in the software supply chain.
Third-party software libraries introduce a large attack surface. This has long been a security challenge across systems before web3, for example with the log4j exploit, which affected widespread web server software, last December. Attackers will scan the internet for known vulnerabilities to find unpatched issues they can exploit.
Imported code may not be written by your own engineering team, but its upkeep is critical. Teams must monitor their software’s component parts for vulnerabilities, ensure updates are deployed, and keep up to date on the momentum and health of the projects on which they depend. The real and instant cost of exploits for web3 software vulnerabilities makes it challenging to responsibly communicate these issues to library users. The verdict is still out as to how or where teams communicate these to one another in a manner that doesn’t accidentally put user funds at risk.
- Examples
- Wormhole bridge hack
- Multichain vulnerability disclosure hack
- Profile
- Who: Organized groups such as APTs, solo actors, and insiders.
- Sophistication: Moderate (need technical know-how and some time).
- Automatability: Moderate (scanning to find faulty software components can be automated; but when new vulnerabilities are discovered, exploits need to be constructed manually).
- Expectations for the future: Supply chain vulnerabilities are likely to increase as the interdependence and complexity of software systems rises. Opportunistic hacking will likely also increase until good, standardized methods of vulnerability disclosure are developed for web3 security.
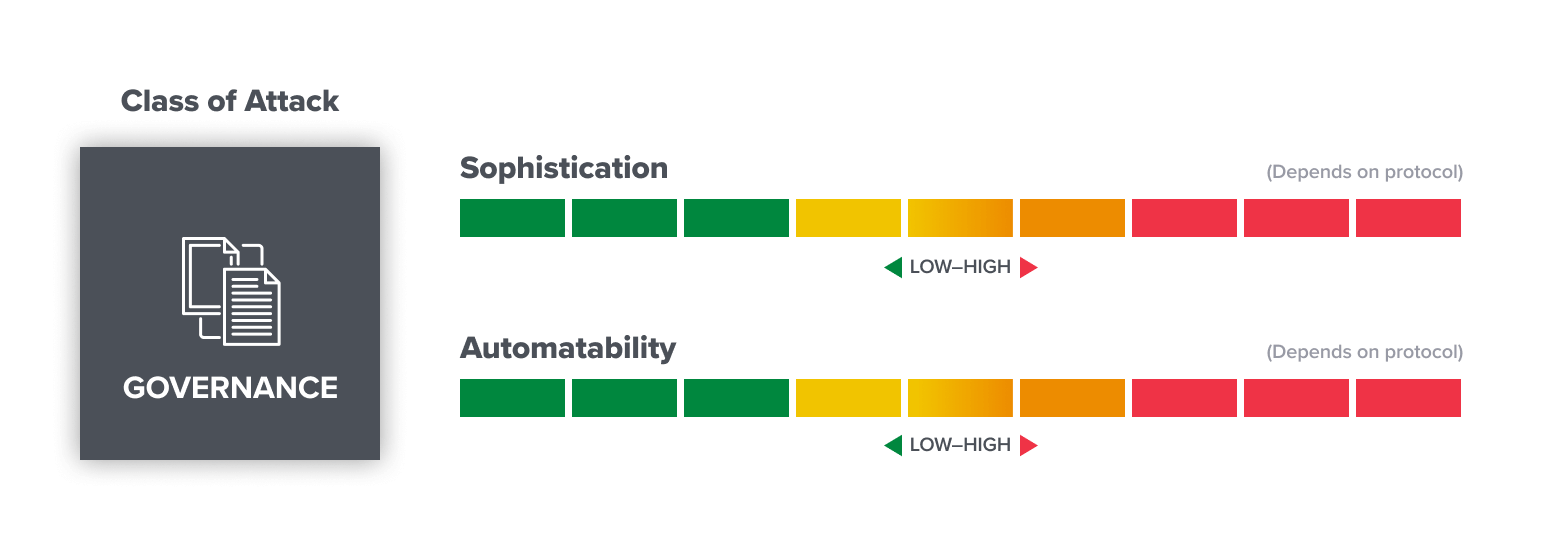
Governance attacks: the election stealers
This is the first crypto-specific issue to make the list. Many projects in web3 include a governance aspect, in which token-holders can put forward and vote on proposals to alter the network. While this presents an opportunity for continual evolution and improvement, it also opens a backdoor to introduce malicious proposals that may damage the network if enacted.
Attackers have devised new methods to circumvent controls, commandeer leadership, and loot treasuries. Once a theoretical concern, governance attacks have now been demonstrated in the wild. Attackers can take out massive “flash loans” to swing votes, as recently happened to the decentralized finance, or DeFi, project Beanstalk. Governance votes that result in automatic execution of proposals are easier for attackers to exploit; whereas, if proposal enactment is subject to a time delay or requires manual sign-off from multiple parties (through a multisig wallet, for example), it can be harder to pull off.
- Examples
- Beanstalk fund-siphoning
- Profile
- Who: Anyone from organized groups (APTs) to solo actors.
- Sophistication: Low-to-High, depending on the protocol. (Many projects have active forums, communities on Twitter and Discord, and delegation dashboards that can easily expose more amateur attempts.)
- Automatability: Low-to-High, depending on the protocol.
- Expectations for the future: These attacks are highly dependent on governance tooling and standards, especially as they relate to monitoring and the process of proposal enactment.
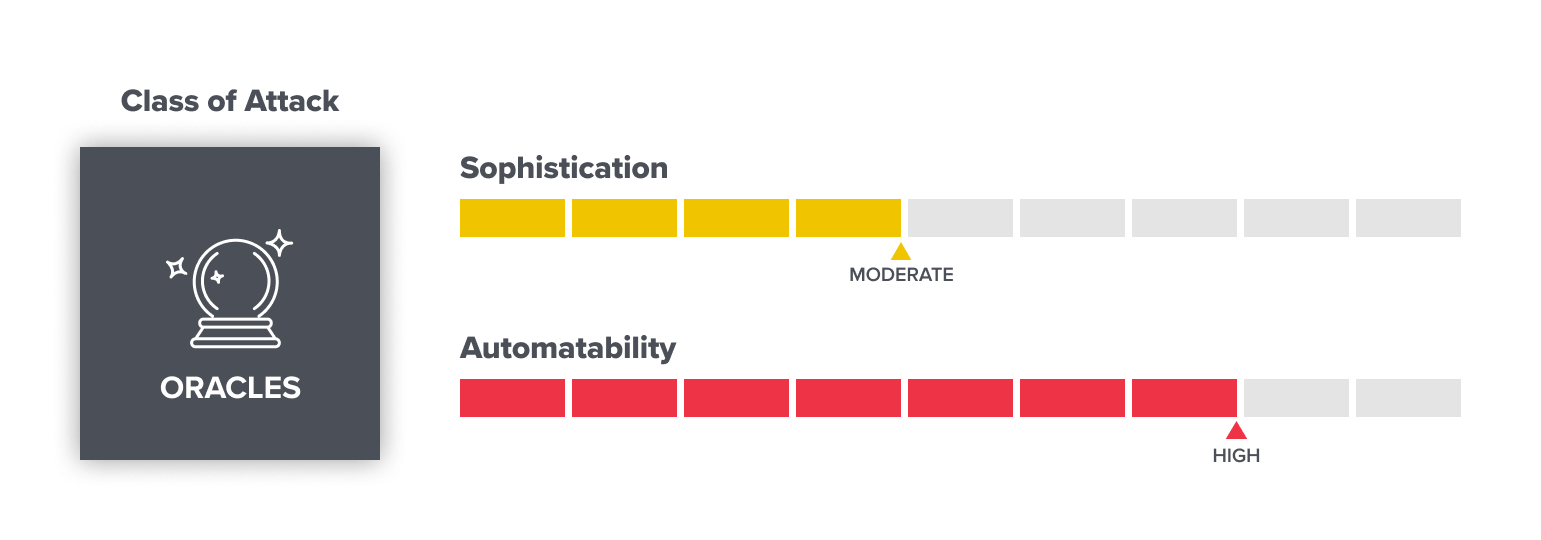
Pricing oracle attacks: market manipulators
Accurately pricing assets is hard. In the traditional trading arena, artificially inflating or deflating the price of an asset through market manipulation is illegal and you can be fined and/or arrested for it. In DeFi, which gives random people the ability to “flash trade” hundreds of millions or billions of dollars, causing sudden price fluctuations, the problem is pronounced.
Many web3 projects rely on “oracles” – systems that provide real-time data and are a source for information that cannot otherwise be found on-chain. Oracles are often used to determine exchange pricing between two assets, for instance. But attackers have found ways to fool these sources of supposed truth.
As the standardization of oracles progresses, there will be safer bridges between the off-chain and on-chain worlds available, and we can expect markets to become more resilient to manipulation attempts. With any luck, this class of attacks may, one day, disappear almost entirely.
- Examples
- Cream market manipulation
- Profile
- Who: Organized groups (APTs), solo actors, and insiders.
- Sophistication: Moderate (technical knowledge required).
- Automatability: High (most attacks likely involve automation detecting an exploitable issue).
- Expectations for the future: Likely to decrease as methods for accurate pricing become more standard.
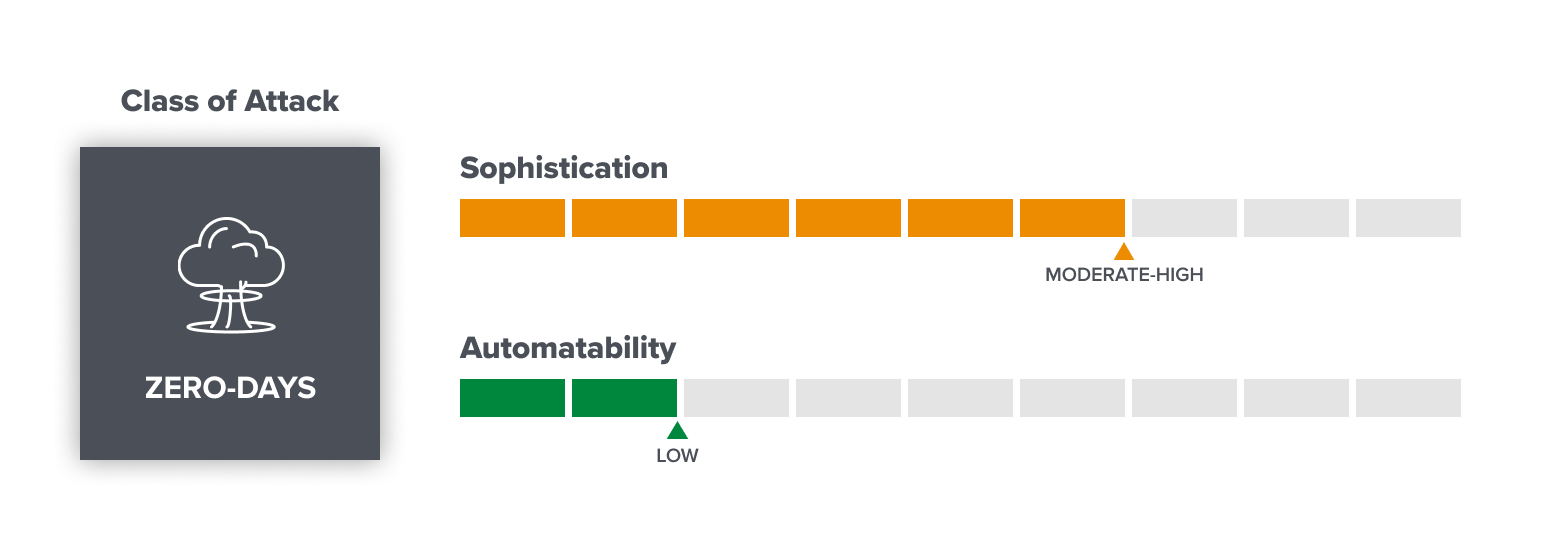
Novel vulnerabilities: unknown unknowns
“Zero-day” exploits – so named because they have been publicly known for zero days at the time of their appearance – are a hot button issue in the field of information security, and it is no different in web3 security. Because they arrive out of the blue, they are the hardest attacks to defend against.
If anything, web3 has made it easier to monetize these expensive, labor-intensive attacks since it can be difficult for people to claw back crypto funds once they’re stolen. Attackers can spend lots of time poring over the code running on-chain applications to find one bug that will justify all their effort. Meanwhile, some once-novel vulnerabilities continue to plague unsuspecting projects; the re-entrancy bug that famously felled TheDAO, an early Ethereum venture, continues to resurface elsewhere today.
It’s unclear how quickly or easily the industry will be able to adapt to triage these types of vulnerabilities, but continued investment in security defenses such as auditing, monitoring, and tooling will increase the cost for attackers seeking to exploit them.
- Examples
- Profile
- Who: Organized groups (APTs), solo actors (less likely), and insiders.
- Sophistication: Moderate-High (technical knowledge is required, but not all the vulnerabilities are too complex for people to understand).
- Automatability: Low (finding novel vulnerabilities takes time and effort and is not likely to be automated; once found, scanning for similar issues across other systems is easier).
- Expectations for the future: More attention attracts more whitehats and makes the “barrier to entry” higher for discovering novel vulnerabilities. Meanwhile, as web3 adoption grows, so does the motive for blackhats to find new exploits. This is likely to remain a game of cat-and-mouse as it has in many other areas of security.
-

Riyaz Faizullabhoy Riyaz Faizullabhoy is CTO of a16z crypto, where he consults the projects in the portfolio with technology and security expertise, and supports the firm's crypto-native operations. Prior to joining a16z crypto, Riyaz co-created the custody solution and served as a technical lead for Facebook's blockc...
-

Matt Gleason is a security engineer for a16z crypto, helping portfolio companies with their application security, incident response, and other audit or security needs.